IAM
Problem Statement
Managing user identities and access to resources has become increasingly challenging. Users face challenges such as assigning a Developer role to a member then the member has access to all applications within a workspace, leading to increased risk, lack of roles, and other challenges. This makes it difficult to handle resources, user roles, permissions, and stay ahead of security threats.
Introduction of IAM 2.0
To address these issues, we have introduced “IAM 2.0” in beta version, a new feature designed to simplify identity management, enhance security, and ensure compliance. IAM 2.0 ensures that the right individuals have the appropriate access to resources, safeguarding both organizational data and the platform.
Key Features
While designing IAM 2.0, we focused on the following four key areas:
- Manage Complexity in Identity Management
- Ensuring secure and appropriate access for a large number of users.
- Handling various access levels and permissions across different user roles.
- Managing access to numerous and diverse resources efficiently.
- Manage Access Controls
- Addressing IAM systems that do not meet current market standards and lack user management and integration capabilities.
- Enhancing role granularity for access control and ensuring adequate separation of duties.
- Manage Security Risks
- Preventing unauthorized access to sensitive data or systems through controlled permissions.
- Solve the User Experience Concerns
- Simplifying user journeys to reduce confusion and frustration in navigating access requests and managing profiles.
- Scaling IAM systems to handle increased user volumes and diverse access needs.
New Features in IAM 2.0
IAM 2.0 introduces three new tabs to streamline identity and access management:
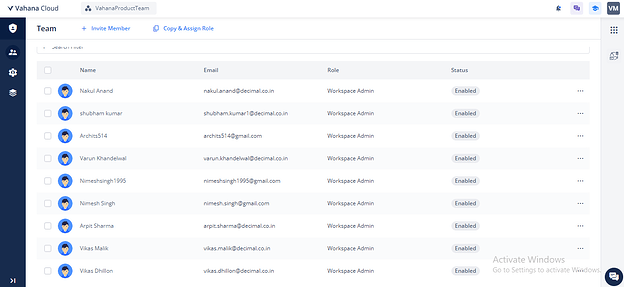
- Team Management: Invite team members and manage access for existing members within a workspace.
- Assign Roles & Resources: Grant two permission exceptions under specific conditions.
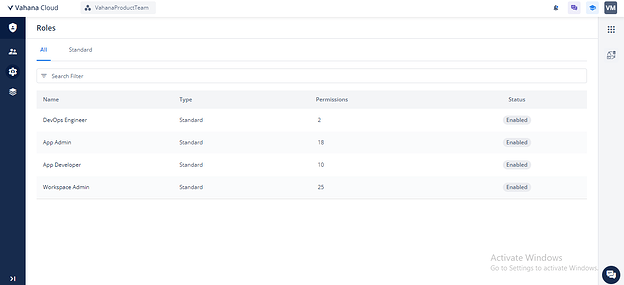
- Users can manage roles along with their permissions. IAM 2.0 includes a set of predefined permissions mapped to the following standard roles:
- Account Owner
- Workspace Owner
- Workspace Admin
- App Admin
- App Developer
- DevOps Engineer
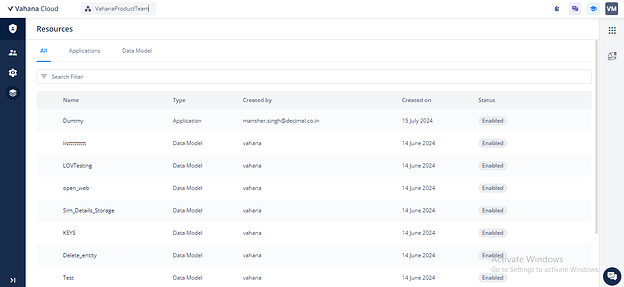
- Users can associate members with resources, allowing users to manage resources through this tab. This includes adding or removing members and viewing all members associated with the current resource. The list of resources introduced in IAM 2.0 includes:
- Application
- Data Modeler
- Theme
IAM 2.0 is a robust solution designed to tackle the complexities of identity and access management. By focusing on security, ease of use, and compliance, IAM 2.0 ensures that your organization can manage user identities and access to resources effectively and securely.
Business Use Cases
- Users can assign access to specific resources to the right individuals, and only those resources will be visible on their dashboard.
- Users can build their team based on the project and assign appropriate roles to each member.
- Users have the ability to grant access to specific branches to the appropriate users based on their roles.
- Users can also grant deployment access for the frontend IAM and manage environment access control through the middleware IAM.
Known Issues
- There is currently no direct option to change the workspace owner; users must raise a support ticket to make this change.
- Users without access to certain tools can still view them but cannot save any changes(This apply only for DevOps Engineer Role)
- Workspace admins have the ability to delete or edit other workspace admins, which can lead to unintended modifications.
- DevOps engineers can commit the application with view access to the application.
- UI issue in the resource tab’s table row.
- Disable resource functionality is not working.
- The resource order is inconsistent when assigning a second role to users. For example, the first role follows the order: Application/Theme/Data Modeler, while the second role follows a different order: Theme/Data Modeler/Application.
- On the resource dashboard page, when a user clicks on the heading box of the resource members table, the UI misbehaves by selecting all members, but this selection is not visually reflected on the UI.
Note
- Users may encounter instability issues during the edit member journey.
- Please avoid using the DevOps Engineer role.
Click here to learn more about IAM 2.0.